December 1, 2022
I started today’s newsletter by typing in “December 1” and then taking five to just repeat “WTF? December? How? WTF…”


-
-
This paper was linked in an earlier newsletter. Here’s a nice summary and another link to the paper.




-





-

-
Bypass CrowdStrike Falcon EDR protection against process dump like lsass.exe 🤔
“TL;DR Do a memory dump of the RAM with any forensics tool like (dumpit.exe, MAGNET RAM Capture ) and from the dump extract the lsass process using volatility or extract the hashed directly from it.”
https://infosec.exchange/@raptor/109431508345685709
-
Here’s a look at the various pieces of proposed legislation that impact E2EE. Spoiler alert: They all suck.


-

-

-


-
Ping! Ping! 😂

-


-


-







-
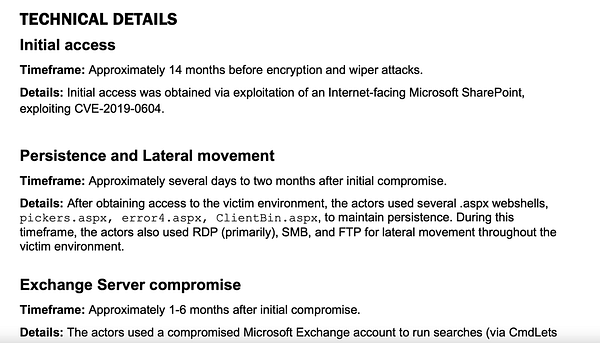
Someone sent in the complete exploitation framework for a collection of 0days that were used from 2018 until probably 2021/22. This is some good intel for people who are tracking bug collisions. It seems that some were killed by internal bug fixes, but they were alive for quite a while first.
But, really, wtf! Someone turned over the entire exploit framework along with additional exploits. It’s wild. What’s the story here?? I’d love to know.

-






-





-





