On war and cybers, some thoughts
The first reports are now coming out about the offensive cyber operations of the Ukrainian intelligence services. Apparently they’re very interested in the Russian government. I’m as shocked as you are.
Please like and subscribe.
The more important lesson to learn here is that espionage is more useful than effects operations conducted without context. What I mean by that is, effects operations are most effective when employed within a strategy that takes advantage of them. Effects operations executed at random are generally speaking of negative value — they train the opposition and burn access.
Intelligence is almost always useful. Effects are useful inside a strategic context. Information operations are orthogonal because they typically don’t involve the same resources.
This focus on espionage demonstrates that Ukraine is focussed on getting the most value from their limited resources. They don’t have the same sort of cyber forces available as the Russians.
Ukraine has limited resources and must get maximum value from what they have. That means espionage.
-


-
Using openAI chat for phishing
https://www.richardosgood.com/posts/using-openai-chat-for-phishing/
-
Sad day for pre Pwn2Own bugs.
https://www.synacktiv.com/publications/cool-vulns-dont-live-long-netgear-and-pwn2own.html
-
This is absolutely hilarious.
A researcher created a bunch of research reports about vulnerabilities that weren’t actually vulnerabilities. And for an alleged RCE they included a broken PoC (it even hits the wrong web page). The developers off the Moobot malware (some sort of Mirai-alike) used the PoC to add support for this fake vulnerability!!
https://vulncheck.com/blog/moobot-uses-fake-vulnerability
-

-
-
-

-
-
Secure messaging is more complex than “use libsignal.”
https://mjg59.dreamwidth.org/62598.html
-
—
-
Here’s a reminder that there’s a really good collection of offense focused security talks bit-rotting away in the old Immunity Vimeo account, e.g.[see below]… not sure if they’ll be up forever since many of the original folks are no longer with the company, so probably worth grabbing before they completely go the way of the dodo.
https://emacs.ch/@anticomputer/109487317977257354
-















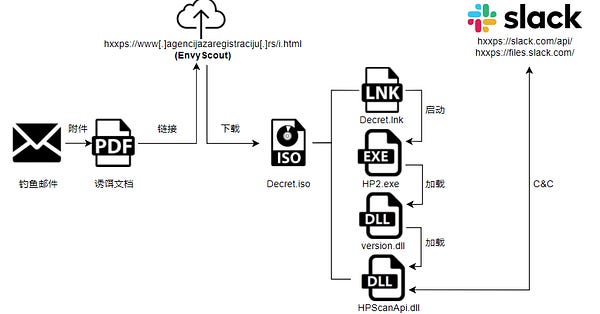
That Cloud Atlas uses techniques which would be laughed at western red team firms shows how big of cyber defence capability spectrum exists. Clearly these techniques work - otherwise they’d be discontinued.
The target organisations almost certainly are not on any of the big clouds which have lots of built in security and demonstrate that to maintain good security on prem requires lots and lots of manpower.