May 20, 2022
Huge news. The Feds won’t use the CFAA to go after security researchers, pinky promise!

Very important caveat.

The EFF is all over it.


https://arxiv.org/abs/2205.07759
There are so many problems with this paper I’m not sure where to start. I guess I’ll start with the conclusion: they are correct. Many APTs use public vulnerabilities rather than 0day.
A short summary of some problems with the paper. Their goal when writing this paper was to answer the question “does timely patch protect an enterprise against APT threats? If so, how timely?” Keep this in mind, they’re thinking about enterprises and patching.
So an early problem is that they assume APTs are an ontological unit. They are not. The term “APT” is a broad generalisation used to collectively refer to many different kinds of these actor.
Another issue is that they assume the reports from as far back as 2008 are reliable, which I am not sure is a safe assumption.
The paper uses APT clusters which are known to be flawed. For example, the WINTI group was more of an umbrella term for different people using the same tools from a particular vendor. Much like one could talk about the “REvil group” to collectively refer to everyone using that ransomware brand, the reality is that affiliates each have different threat profiles. What they use post exploitation says nothing about how they gain access.
These are more epistemology failures.
Understanding campaigns is complicated. Firstly, for a nation state the purpose of breaking into a computer is to do something after breaking in. Gaining access is just step 0. A chore that needs to be done before moving on to the scut work of cyber espionage.
They need to gain access, but they don’t have many concerns about *how* they gain access. Of course, cheaper is better, and faster is better, but those are just guidelines. There are many conditions which could change the calculus here, such as expediency, security, time pressure, resource constraints, procurement pipeline issues, and so on.
For the majority of cases though, they can use whatever works and just get on with the job. Not every operation is about disrupting an adversary before a deadline.


The EU is intent on fucking up a critical thing for a theoretically noble reason in a very dumb way.


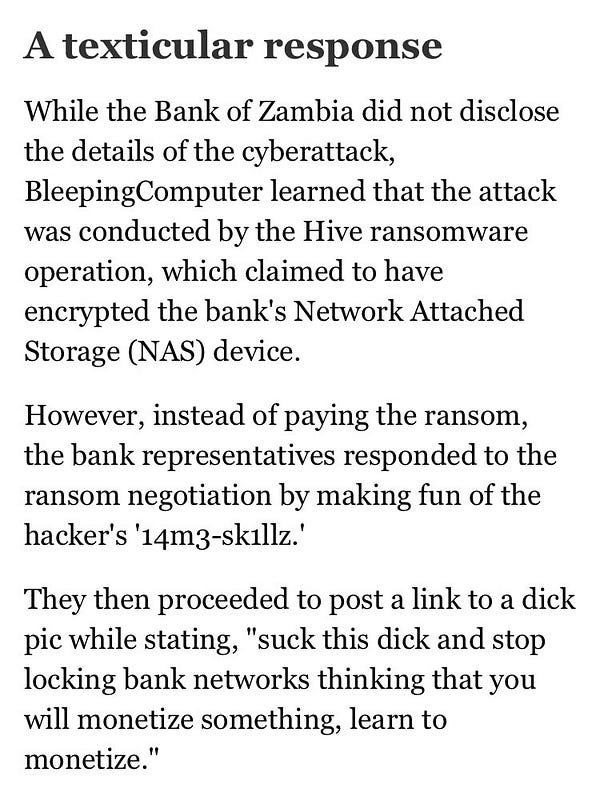
Update your incident response handling to include better messaging to attackers.
Twitter is on the case for Ukraine disinformation
If Halvar has seen further it is because he is a giant. Possibly standing on his own shoulders.

-

Here’s a PDF book (short) on The Trust, an incredibly effective counterintelligence operation run by the Cheka (earliest incarnation of the KGB).
https://jmw.typepad.com/files/simpkins---the-trust-security-intelligence-foundation.pdf
Here’s another document on the same topic, because it is really an awesome op.
https://www.centerforintelligencestudies.org/the-trust.html
-
Reviews from the front lines on what matters in equipment,




-
ESET finding more Russian malware


-
Supply chain attacks. Trust is the root of all compromise…


-
The future is kinda crazy. Costa Rica is at war with Conti.
https://www.bbc.co.uk/news/technology-61323402
-
Russian offensive cyber supply chain


-
Strongmen regimes and military blunders.
https://warontherocks.com/2022/05/when-strongmen-invade-they-bring-their-pathologies-with-them/